Web Phishing vs. Web Fishing: Unraveling the Catch in the Digital Deception Game
Web Phishing vs. Web Fishing: Unraveling the Catch in the Digital Deception Game
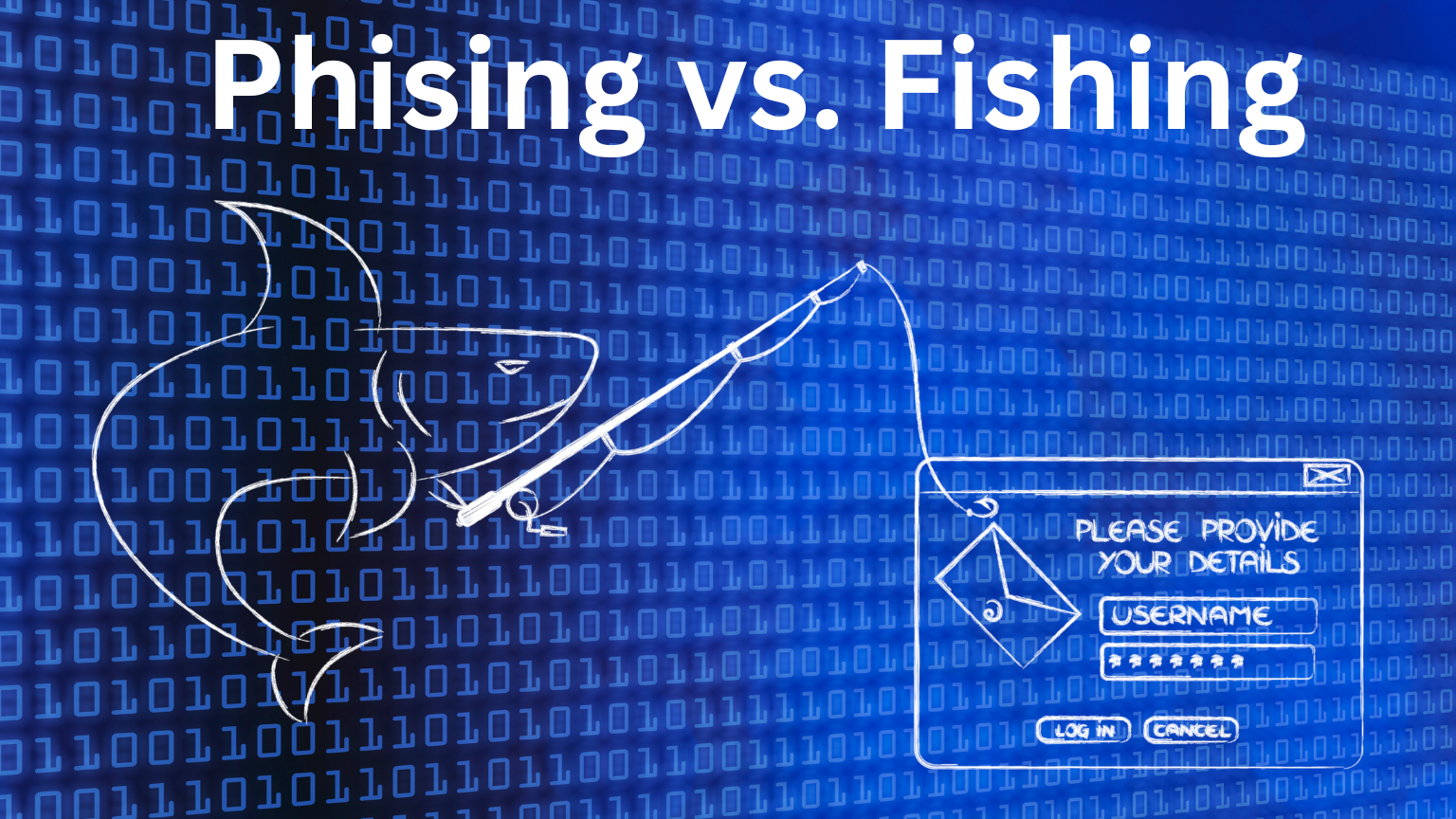
When navigating the perilous waters of online trust, two deceptive practices stand out: web phishing and web fishing. Though often mistakenly used interchangeably, these cyber threats exploit distinct psychological leverages and pathogenic tactics—one cloaked in urgency, the other in subtle lures—making understanding their differences more than just informative; it’s essential for digital survival. Far from mere buzzword noise, “phishing” and “fishing” paint a vivid dramatization of how scammers bait victims, each employing unique patterns to reel in unsuspecting clicks.
The distinction—imperceptible yet profound—can mean the difference between a secure session and a compromised device.
At the heart of the divide lies intent and method. Web phishing operates like a digital fisherman casting a wide net across cyberspace.
Its architects craft convincing replicas of trusted websites—banks, retailers, or service platforms—with flawless logos, authentic-looking interfaces, and urgent messages: “Your account has been locked. Verify now.”
Phishing attacks exploit trust, often relying on fear or curiosity to prompt immediate action. Victims are lured into entering credentials, downloading malware, or authorizing fraudulent transfers under the guise of legitimacy.
“The deception isn’t in complexity—it’s in consistency,” notes cybersecurity expert Dr. Elena Ramirez. “A phishing email mimics official language, mimics branding, and creates high-pressure timelines to override caution.” Phishing thrives on volume: millions of emails sent daily, hoping a small percentage of targets bite.
Web fishing, by contrast, is a precise, targeted approach—like a seasoned angler baiting a specific fish with a custom hook—and it’s exactly what spear fishing scammers use.
Web fishing—sometimes called “spear phishing”—leans into personalized details to create believable, tailored traps. Rather than raw noise, it uses reconnaissance: social media profiles, public records, or data breaches to harvest names, job titles, recent activities, or personal interests. The result is email or message that says, “Hi Sarah, we noticed your recent travel to Paris—your account access was flagged.
Confirm your trip details immediately.” This hyper-specificity lowers cognitive resistance, making navigation into digital bait far easier.
While phishing casts a wide net with generic templates, web fishing crafts a line with pinpoint accuracy. The phisher aims for mass infiltration; the web fisher focuses a hook on a single, vulnerable catch. Both aim to reel in victims, but their techniques betray fundamentally different psychological strategies:
- Phishing: Broad Strokes of Urgency and Fear – Designed to trigger knee-jerk reactions.
A reset deadline, a suspicious login alert, or a celebrity-themed scam leverages stress and panic. Respond without thinking, and the scam succeeds.
- Web Fishing: Intimate Tactics of Social Engineering – Uses personalization to foster a false sense of trust. By mirroring a recipient’s real-world identity, the lure bypasses skepticism, making the deception harder to detect.
Common vectors illustrate the divergence clearly.
Phishing often arrives via deceptive links in emails or SMS: clicking appears harmless, but it redirects to fake login pages designed to harvest passwords. Social media DMs posing as IT support or delivery services deliver similar gambits.
Web fishing, conversely, may begin with a personalized message referencing a mutual contact, recent group event, or geographic detail—then poses an urgent request: “Hi Mark, your colleague from Chicago is tracking a file you recently shared. Confirm if you requested its access?” These messages blend factual credibility with plausible scenarios to quiet digital defense.
To effectively counter these threats, recognizing the catch—and knowing which line contains which bait—is imperative.
Phishing phishing—the broad, impersonal storm seeking high volume of victims—requires vigilance:** always verify sender addresses, avoid automatic clicks, and never input credentials on unverified pages. But web fishing demands sharper focus: pause and assess: Is this message referencing *your* known life? Does it request unusual or sensitive actions?
Verifying personal data before responding slows the intimacy scammers rely on.
Protective measures include multi-factor authentication, browser warnings, and email filtering systems that flag anomalies. Yet human judgment remains the strongest defense: skepticism isn’t cynicism, it’s survival in a crafty landscape.
The distinction between web phishing and web fishing isn’t academic—it’s operational and strategic. Phishing thrives on speed and scale, overwhelming vigilance with noise.
Web fishing exploits patience and specificity, turning personal data into a hook. Understanding these dynamics transforms users from passive targets into informed defenders. In an age where digital fraud evolves rapidly, knowing what’s lurking beneath the surface isn’t just smart—it’s survival.



Related Post

Okinawa’s Military Bases at a Crossroads: The Enduring Controversy of the U.S. Presence

Carmelo Anthony’s Stature: High-Impact Heights That Redefined a Basketball Legacy

Ny Powerball Results Latest Numbers Ignite Anticipation – Winning Tickets Unveiled in Latest Mega Match

Livvy Nudes: The Cultural Impact of a Controversial Digital Phenomenon

