Take Control: Master Your Digital Footprint with View and Manage Your Gmail Activity
Take Control: Master Your Digital Footprint with View and Manage Your Gmail Activity
In an era where every click, search, and login leaves a trace, managing your digital footprint is no longer optional—it’s essential. Your Gmail activity, encompassing sent emails, clicked links, attachments, and even prolonged app interactions, forms a detailed record of your online behavior. Understanding how to view and manage this activity empowers you to protect privacy, boost security, and maintain control over how your digital persona is perceived.
This comprehensive guide unravels the essentials of inspecting and managing your Gmail activity, offering clear steps and practical insights for users at every tech proficiency level.
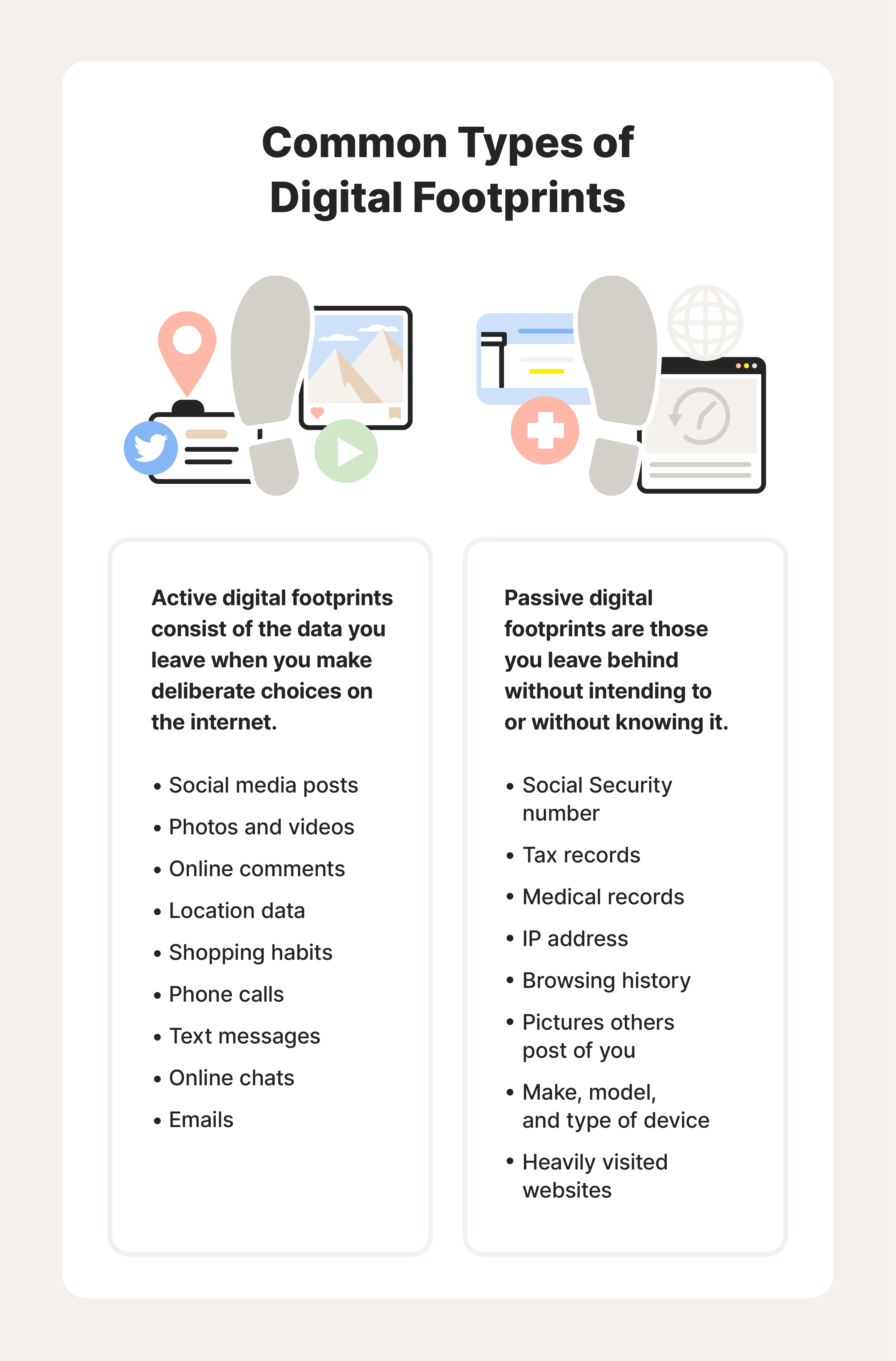
Why Viewing Your Gmail Activity Matters: Every email you send and reception you make generates a data trail. From collaboration tools to personal correspondence, your Gmail usage reflects work habits, social connections, and sensitive information exposure.
“Your email is not neutral—it’s a window into your digital life,” says cybersecurity expert Elena Torres. “Being aware of what’s logged gives you strategic leverage.” Without visibility, users remain vulnerable to identity theft, phishing, or unintended disclosure. Regular review transforms passive data retention into active digital stewardship.
Accessing Your Gmail Activity: Tools and Settings
Step 1: Open Safe-Browsing and Activity Logs via Your Gmail Interface To begin, navigate to your Gmail account through your preferred browser or the official app. Though direct access to a centralized “Activity” dashboard is limited compared to newer platforms, a multi-layered approach unlocks visibility. - Sign in to your Gmail via desktop for optimal detail.- Click the less-obvious tag or icon—often located in the top menu or near the search bar—labeled something like “Manage Account” or “Security settings.” This path may vary by platform update, so look for indicators like profile customization options or session logs. - Within security settings, locate activity logs linked to email interactions, sent messages, and app integrations. These logs are often accessed via “See all activity” options hidden under advanced privacy controls.
- Enable automated alerts for unusual login places or suspicious activity patterns to stay ahead.
Understanding What Is Tracked: Gmail activity logs capture more than just message content. They include timestamps of sends and opens, metadata like IP addresses, connection timestamps, linked third-party app interactions (e.g., Calendar sync, email templates), and even cursor clicks within Gmail interfaces in some account setups.
The IETF’s RFC 8412 and internal security documents confirm that cloud email services classify such behavioral data as critical metadata for threat detection—but equally vital for user transparency.
How to View and Interpret Your Activity History
Once logged in, users gain granular insights into their Gmail behavior through structured data panels. Viewing your activity involves cross-referencing timestamps, recipients, and app references to reconstruct digital interactions.
For instance, a spike in outbound mail followed by a login from an unfamiliar country may signal compromised credentials.
To interpret your activity effectively: - Filter logs by date range to isolate recent or historical activity. - Compare expected email patterns with detected anomalies—unrecognized recipients, unexpected attachment sizes, or sudden time-zone mismatches warrant deeper scrutiny.
- Export logs into CSV or PDF formats for archival or forensic review. - Pair this data with device and browser history to map full user pathways across devices and sessions.
Best Practices for Tracking and Managing Activity
- Schedule Weekly Reviews: Dedicate 10–15 minutes each week to sift through logs.Consistency prevents data creep and ensures timely response to threats. - Enable Two-Factor Authentication (2FA): Adds a critical layer—even if activity logs reveal access attempts, 2FA blocks unauthorized entry. - Use Strong, Unique Passwords: Manage them via dedicated password managers linked to your Gmail app or browser syncing tools.
- Review Attachment and Link Permissions: Be mindful that links clicked in emails trigger activity tracking. Hover before clicking to preview URLs, and avoid suspicious short links. - Audit Connected Apps: Through Gmail’s “Apps” settings, revoke unnecessary third-party integrations that access account data, reducing potential exposure points.
Advanced Management: Export, Search, and Secure Deletion
Beyond daily logs, users can claims deeper control through export and deletion capabilities. These tools support compliance, digital hygiene, and legacy record preservation. - Export Activity Data: Access via Gmail settings under “Security” or “Export”—use secure formats (e.g., encrypted .zip) and encrypted cloud storage for transport.
This enables personal archiving or legal discovery. - Search Across Activity Dates: Leverage Gmail’s powerful search syntax—e.g., time ranges combined with keywords (“2024-08 outgoing from Germany”)—to pinpoint high-risk events quickly. - Secure Permanent Deletion: For sensitive messages or activity trails, use Gmail’s “Purge” option sparingly; full removal requires confirming deletion of all replicas, including cached copies in third-party backups.
Always verify through confirmation prompts before irreversible actions.
Privacy Implications and Ethical Considerations
Transparency in viewing activity brings responsibility. While Gmail’s design aims to protect user data, the information collected—though often anonymized—can be accessed internally by service providers.Users should: - Read privacy policies carefully to understand how logs are stored, shared, and retained. - Opt into privacy-focused features when available, such as incognito email sending or activity logging opt-outs (where supported). - Be aware that sharing trusted logs with certified auditors or legal authorities upholds both personal security and regulatory compliance (GDPR, CCPA).
Real-World Scenarios: Why Monitoring Gmail Activity Protects You
Consider a freelance


Related Post

Buona Domenica: What Does “Buona Domenica” Really Mean in English?

Breaking Free from Movies2Watch.tv: Top Legal Streaming Alternatives in 2024
2025’s Unexpected Hollywood Anomaly: Pixar Boy Abducted by Aliens—and the Eerie Pixar Employee Coincidence

How to Unlock Lock Combination: Master the Art of Cracking Security Pins with Precision

