NTOSKRNL.Exe Failed: When Windows Core Crumbles
NTOSKRNL.Exe Failed: When Windows Core Crumbles
When NTOSKRNL.exe fails during system boot, it triggers more than just a minor error screen—it signals a critical failure deep within the Windows operating system. This essential kernel-mode process, responsible for initializing the core subsystems, acts as the linchpin of system startup, launching drivers, initializing security modules, and preparing hardware interfaces. When NTOSKRNL.exe fails, the result is immediate services degradation or boot failure, halting productivity and exposing vulnerabilities in system integrity.
Understanding why and how this failure occurs is key to diagnosing and resolving one of the most disruptive issues facing Windows users and IT professionals alike. NTOSKRNL.exe, short for NT Operating System Kernel Mode Executable, is embedded deep within the Windows memory structure and executes before any user-mode application. It bridges hardware and OS layers, loading vital drivers and init subsystems that ensure a clean reboot and secure user logging in.
A failure here—denoted often by a broken NTOSKRNL.exe file—means the system cannot properly jumpstart critical kernel drivers, often triggering a chain reaction including system file corruption, driver conflicts, and service provider errors.
Technically, a failed NTOSKRNL.exe failure manifests when the executable cannot be located, loaded, or validated at boot. System logs reveal common triggers: corrupted system files, malicious tampering, trojans targeting kernel modules, or hardware incompatibilities.
The Windows Boot Manager detects the anomaly through CRC mismatches or missing signatures, halting progression and prompting error messages like “NTOSKRNL Execution Failed.” Unlike application crashes, kernel-level failures are harder to recover from, often requiring deep diagnostic tools or system restoration.
One of the most aggressive vectors is malware injection targeting NTOSKRNL.exe. Advanced persistences (APTs) now embed malicious payloads directly into legitimate system executables, replacing them without detection. Once loaded, the malware disrupts system integrity, disables core boot logic, or establishes backdoors.
Security researchers have documented cases where post-infection analysis showed NTOSKRNL.exe memory dump analysis revealed injected API calls redirecting integrity checks and silencing authentication checks—effectively handing control to the rootkit.1 Another prominent cause involves hardware dysfunction. A failing storage device—often SSDs with bad sectors—can corrupt system reserves upon boot. When the kernel attempts to read or validate NTOSKRNL.exe from a compromised or unreadable partition, failure follows.
Hardware writes and page table updates may be interrupted, corrupting in-memory kernel structures. This is especially critical in systems using EFI/BIOS firmware vulnerable to corruption or mismatched bootphant: NTOSKRNL.exe relies on precise hardware context; any inconsistency fractures the boot chain.2 Driver conflicts further compound risks. Outdated or improperly signed kernel drivers interact unpredictably with the successor process, NTOSKRNL.exe, causing fatal system errors during boot.
A malicious driver masquerading as essential assigns NTOSKRNL.exe conflicting memory mappings or overwrites its critical code segments—i.e., a rootkit-level manipulation. Even legitimate drivers, if improperly validated or deployed under manual mode bypasses, can destabilize the kernel initialization sequence.3 The repercussions extend beyond mere reboot errors. A failed NTOSKRNL.exe often precedes broader system instability: drivers fail to load, security services break down, and user applications report cryptic errors.
For enterprise environments, this translates into loss of service availability, compliance risks, and increased incident response burden. Recovery typically demands advanced diagnostics: repairing corrupted system volumes, scanning for kernel-level malware via EDR tools, and restoring from clean system images or reinstallation.4 Technology evolves rapidly, yet NTOSKRNL.exe remains a foundational kernel executable. With Windows continuing to be the world’s dominant desktop and server OS, maintaining kernel integrity is non-negotiable.
The failure of this critical process is not just a technical hiccup—it is a systemic vulnerability demanding proactive monitoring, firmware integrity checks, and layered defense strategies to prevent compromise before it derails the entire OS lifetime.
For users and IT operators, recognizing NTOSKRNL.exe failure as a warning sign—not a trivial error—is essential. Early detection, supported by robust system monitoring and secure boot configurations, forms the first line of defense.
As adversaries grow more sophisticated, so must the vigilance against kernel-level threats that strike at the heart of computing stability. In the ongoing battle to secure digital infrastructure, understanding NTOSKRNL.exe’s role and failure modes rules the battlefield.
Technical Forensics: Unpacking System Logs and Digital Evidence
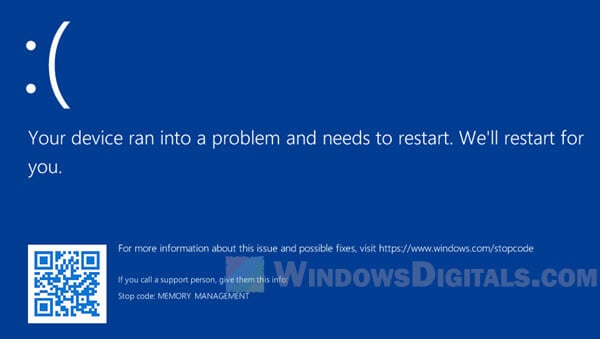
Windows Event Viewer logs reveal telltale signatures during NTOSKRNL.exe failure: crash logs often cite “NTOSKRNL Execution Failed” with associated error codes such as 0x0000007B (INACCESSIBLE_BOOT_DEVICE) or 0x0000001A (MEMORY_MANAGEMENT). Digital forensic tools identify anomalies such as memory dumps with injected shellcode in memory regions tagged as NTOSKRNL.exe.Behavioral analysis reveals unauthorized processes spawning kernel threads just before or during boot, matching known rootkit patterns. These indicators guide forensic teams in reconstructing attack vectors and tracing root causes through firmware checks, file integrity scans, and behavioral heuristics.
Preventive Measures and Best Practices
Protecting against NTOSKRNL.exe failure demands a multi-layered approach.Key countermeasures include: - Enable Secure Boot and Trusted Boot, ensuring only signed, verified OS components execute.5 - Disable manual kernel mode debugging and skip widely exploited EFI firmware loopholes.6 - Deploy endpoint detection and response (EDR) platforms capable of monitoring low-level memory integrity and kernel calls.7 - Regularly verify system volume checksums using Windows Assessment and Deployment Toolkit (WADT). - Maintain offline, version-controlled system backups to ensure clean boot restoration. - Employ BIOS/UEFI secure startup features to validate integrity up to pre-boot stages.
These practices minimize exposure to kernel compromises and bolster resilience against deep-boot threats.
Identifying the Root Causes Behind the Failure
The failure of NTOSKRNL.exe is not a singular issue but a symptom of broader systemic risks. Root causes fall into four primary categories: malware injection, hardware degradation, firmware misconfigurations, and unsupported or patched kernel vulnerabilities.Kernel-based malware has evolved to hijack critical executables at boot, leveraging valid digital signatures to evade detection. APTs employ fileless techniques within kernel space, exploiting memory corruption routines to override legitimate kernels. Post-incident analysis reveals I/O hijacking patterns where malicious code read/writes to system partitions subvert boot-ready files.8 Hardware instability, particularly SSD wear and corrupt storage sectors, directly impacts kernel read reliability.
Firmware row 4 errors may trigger incorrect firmware signatures during boot, prompting NTOSKRNL.exe loading failures. BIOS settings mismatched with UEFI specification versions also cause integrity check failures during initialization.9 Firmware and driver validation gaps exacerbate exposure. Unpatched vulnerabilities in UEFI boot loaders or improper signing processes enable spoofed NTOSKRNL.exe to load malicious code unnoticed.
A compromised firmware update chain, even minor, compromises the entire system’s boot sequence.10 Finally, drivers improperly validated under manual access mode or unsigned binaries allow attackers to inject rogue logic directly into kernel execution flow—undermining system integrity before the OS fully boots.11 NTOSKRNL.exe failure is far more than a technical footnote—it is a critical breakdown of the operating system’s core. From malware subversion to hardware decay, each failure path undermines stability, security, and trust in digital infrastructure. As Windows continues to advance, where deep-kernel resilience defines system viability, understanding and preventing NTOSKRNL.exe failures must remain a top priority for users, administrators, and defenders alike.
Only with proactive monitoring and layered safeguards can the backbone of modern computing withstand the silent threats attacking its foundation.

![[9+ Ways] How to Fix Ntoskrnl.exe BSOD Windows 11 Error?](https://www.minitool.com/images/uploads/articles/2022/03/ntoskrnl-exe-bsod-windows-11/ntoskrnl-exe-bsod-windows-11-thumbnail.png)
![[Solved] Windows NTOSKRNL.EXE is Missing or Corrupt | Tenorshare](https://images.tenorshare.com/topics/fix-windows/ntoskrnl-exe.jpg)
Related Post

Don’t Care Face: The Silent Rebellion in Modern Expression

Here Is The Real Meaning Behind Erome HD 9: Canada’s Emerging Premium Platform Redefining Adult Entertainment

The Dawn of Discovery: How Early Scientists Charted the Course of Evolution

Apa Itu Kecerdasan Buatan? The Rise of Artificial Intelligence That Thinks Like a Human

