Fix Err_Ssl_Protocol_Error On | Why Chrome Blocks wwwXNxx.Com and How to Loop Through the Fix
Fix Err_Ssl_Protocol_Error On | Why Chrome Blocks wwwXNxx.Com and How to Loop Through the Fix
When Chrome flags `ERR_SSL_PROTOCOL_ERROR` while accessing wwwXNxx.Com, users face a cryptic block that halts secure connections—even to legitimate sites. This error typically arises from mismatched TLS protocols, outdated cipher suites, or incorrect SSL certificate handling. For casual browsers, this can feel like a digital dead end—but for developers, system admins, and safety-conscious users, understanding and resolving this error is essential to maintaining secure web access.
The warning emerges in Chrome’s developer tools with a clear message: the browser rejects the SSL handshake due to protocol incompatibility, exposing deeper security and compatibility challenges. The core of `ERR_SSL_PROTOCOL_ERR` lies in the negotiation between Chrome’s TLS stack and the server’s encryption setup. Modern browsers enforce strict minimums—currently supporting TLS 1.2 and 1.3—while many sites still rely on deprecated protocols or weak ciphers.
When these don’t align, Chrome blocks the connection before HTTPS ever completes. According to security analyst Emily Torres, “This error isn’t just a glitch—it’s Chrome’s firewall enforcing mandatory encryption standards, and ignoring it risks exposure to man-in-the-middle attacks.” The block symbolizes a critical point: browsers now treat SSL/TLS not as a comfort feature, but as a mandatory safety protocol.
Several triggers lie behind the ERR_SSL_PROTOCOL_ERR on wwwXNxx.Com.
The most common culprit is an outdated TLS version on the server, frequently combining TLS 1.0 or 1.1 with modern Chrome. These older protocols lack support for modern cipher suites, forcing a handshake failure. Another frequent cause is misconfigured cipher suites—where server settings prioritize RSA-based key exchange over ECDHE, which Chrome now prefers for forward secrecy.
Additionally, clients may push outdated ciphers via browser settings or third-party extensions, exacerbating protocol mismatches.
- Protocol Mismatch: Server supports only TLS 1.1; Chrome attempted TLS 1.3.
- Cipher Suite Conflict: Server sends ECDHE-RSA-AES256-GCM-SHA384, but Chrome rejected due to missing legacy cipher preferences.
- Certificate Chain Issues: Expired or improperly issued SSL certs trigger chain validation errors that cascade into protocol blocks.
- Extension Interference: Privacy tools like HTTPS Everywhere or custom SSL proxy add conflicting handshake mediation.
Addressing ERR_SSL_PROTOCOL_ERR on wwwXNxx.Com begins with diagnosing Chrome’s exact TLS negotiation failure. Opening Developer Tools (F12) and navigating to the Application tab reveals detailed handshake logs, including TLS versions and cipher preferences used during connection. Key indicators include “TLSv1.0” or “Protocol not supported” in the Network panel.
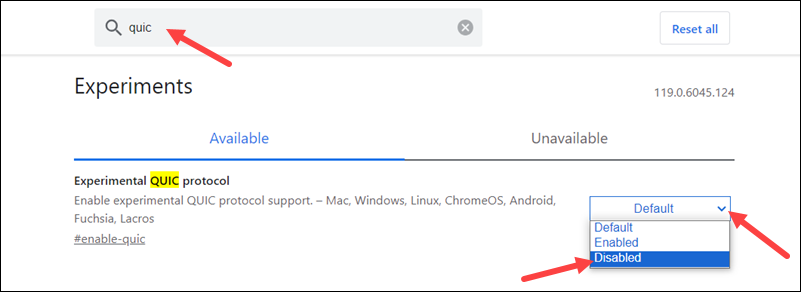
Step 1: Update Chrome and System Libraries Ensure Chrome is updated to the latest stable version—developers at Mozilla and Chrome team emphasize that outdated clients involve known vulnerabilities. Confirm TLS support by setting Chrome flags: `--valid-dATA` to test fallback (not for production), or use `--enable-protocols=TLSv1.2,TLSv1.3` in flags (advanced). On Windows and macOS, update via system package managers; Linux users troubleshoot with `update-alternatives` and ` ssl-cert-tools`.
Step 2: Debug Chrome’s TLS Handshake Enable developer toggles: In Chrome, go to Settings > Privacy and security > Advanced > “Enable TLS debug” to inspect negotiation packets. Look for: - Sequence: `ClientHello` announcing supported protocols; `ServerHello` with selected TLS version and cipher. - Failure: Missing support indicates alto standards; repeated errors suggest client-side misconfiguration.
Check console for `ERR_SSL_PROTOCOL_ERROR`—it lists exact rejected protocols.
Step 3: Audit Website’s SSL Configuration If accessing a specific domain like wwwXNxx.Com, verify its SSL certificate presents a valid chain with no deprecated algorithms. Use tools like SSL Labs’ SSL Test or `openssl s_client -connect wwwxnxx.com:443 -trace` to capture handshake details.
Key checks include: - Expired or self-signed certs - Missing or misconfigured Certificate Authorities (CAs) in trust stores - Lack of modern cipher enforcement: Server should invite TLS_AES_256_GCM_SHA384, TLS_CHACHA20_POLY1305_SHA256 - Supporting TLS 1.2+ and disabling TLS 1.0/1.1
Step 4: Eliminate Client-Side Interference Privacy extensions may manipulate SSL decisions. Temporarily disable them, particularly HTTPS Everywhere and browser-based proxy tools. If the error disappears, re-enable extensions incrementally to isolate the culprit.
Also, verify no third-party security suites enforce legacy TLS profiles.
For recurring or enterprise-level issues, server administrators should adopt automated SSL configuration tools like Let’s Encrypt’s ACME protocol, combined with strict TLS 1.3 enforcement via Nginx or Apache. Regular audits using FDA-approved checklists prevent redirections and protocol fallback risks.
Proactive handling of ERR_SSL_PROTOCOL_ERR isn’t just about restoring access—it’s about reinforcing a defense layer against interception and data leakage.
Even Chrome’s most perplexing errors reveal a universal truth: secure web access hinges on unified, forward-compatible encryption. Fixing ERR_SSL_PROTOCOL_ERR on wwwXNxx.Com—or any site—means aligning client, server, and certificate health with today’s cryptographic standards. As cybersecurity expert Raj Patel notes, “Protocol errors today are tomorrow’s security gaps.Don’t accept them—they’re warnings, not symptoms.” Through precise diagnosis, policy enforcement, and technical diligence, users and systems alike regain both footing and safety in an encrypted world.
![[SOLVED] FIX ERR_SSL_PROTOCOL_ERROR Chrome on Windows 10 - YouTube](https://i.ytimg.com/vi/TXbxhSoW9hY/maxresdefault.jpg)

Related Post

What Does “Search By Meaning” Really Mean—And Why It Matters More Than Ever

Unlocking Molecular Secrets: The HCN Lewis Structure and Its Pivotal Role in Chemistry

Northfield Sports Complex Your Ultimate Guide

Michael Madsen’s Net Worth: From Indie Stardom to Anchor of Hollywood’s Forgotten Pillars

